The IoT device that we’ll be reversing is the Axis M1034-W Network Camera.
Without actually having the camera infront of me to tinker with, we’ll skip a few steps and move on to reversing the firmware.
Grabbing the Firmware:
Google would be ideal since we can’t drop the firmware the hardware way (which makes life easier). Upon hitting the Goo, I came across this link on the first page:
https://www.axis.com/support/firmware
Scrolling down, we can now download the firmware for this application. Thanks axis!
Firmware Analysis:
This firmware is a .bin file, we’ll run the usually commands to see what were working with:
 A file is a named collection of related data that appears to the user as a single, contiguous block of information and that is retained in storage.
A file is a named collection of related data that appears to the user as a single, contiguous block of information and that is retained in storage.
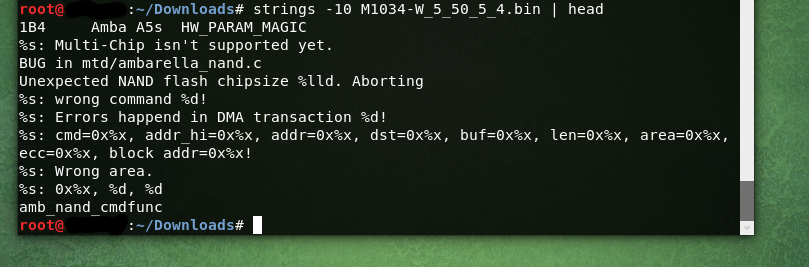 The strings command returns each string of printable characters in files. Its main uses are to determine the contents of and to extract text from binary files. Strings -10 only prints lines with 10bytes or more, I use this to clean up some clutter. Head is after the break to only print the first 10 lines. We can use strings to get more data, but since were only getting the preliminary firmware analysis done, it’s enough info to see the file is intact.
The strings command returns each string of printable characters in files. Its main uses are to determine the contents of and to extract text from binary files. Strings -10 only prints lines with 10bytes or more, I use this to clean up some clutter. Head is after the break to only print the first 10 lines. We can use strings to get more data, but since were only getting the preliminary firmware analysis done, it’s enough info to see the file is intact.
Anyone say binwalk?:
binwalk is a tool for searching a given binary image for embedded files and executable code. Specifically, it is designed for identifying files and code embedded inside of firmware images.
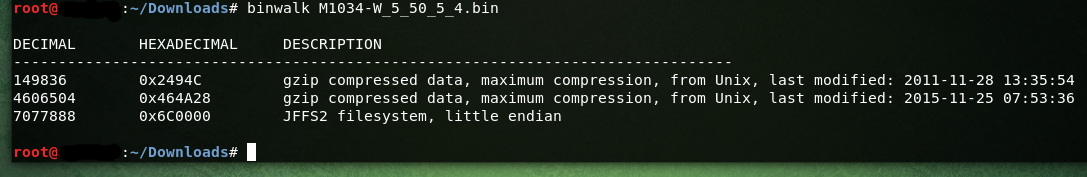 Binwalk gave us some details regarding the filesystem that is inside the bin file: JFFS2 filesystem, little endian aka Journalling Flash File System version 2
Binwalk gave us some details regarding the filesystem that is inside the bin file: JFFS2 filesystem, little endian aka Journalling Flash File System version 2
Since I have delt with this type of filesystem before in other firmwares, I learn to speed things up. We’ll first need to grab a tool called Jefferson
After you install the application and dependencies, we’ll now use binwalk command with a few arguments.
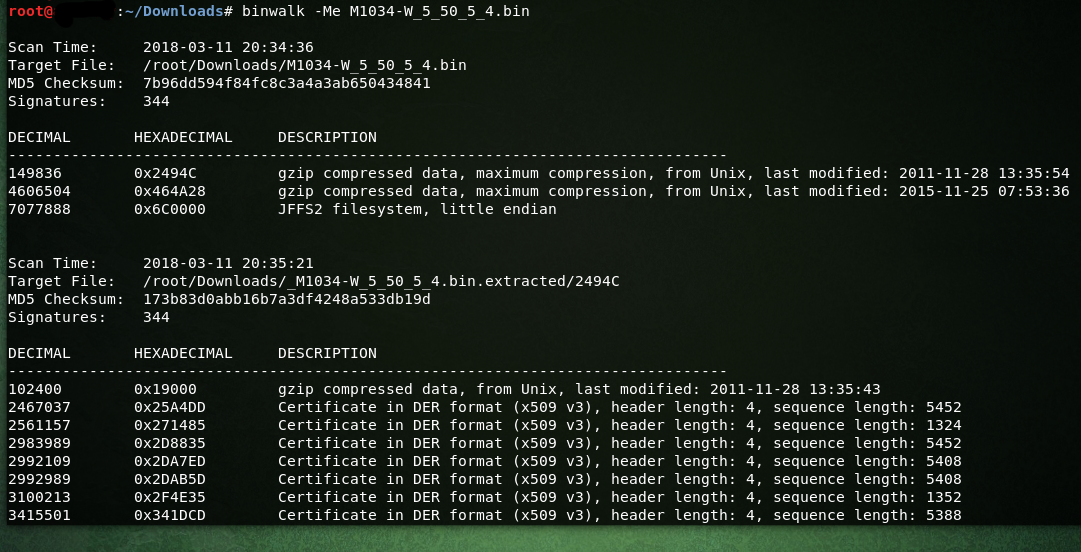 In here I used binwalk -Me,
-M = means to Recursively scan extracted files.
-e = Automatically extract known file types.
In here I used binwalk -Me,
-M = means to Recursively scan extracted files.
-e = Automatically extract known file types.
We needed Jefferson to help with the extraction for an All-In-One extraction of the JFFS2 filesystem.
Show me the GOODS:
After the extraction, open the extracted dir and welcome to filesystem:
From here, we can go through the system looking for key material that will help with moving forward.
Example: Lets see whats in /etc/passwd
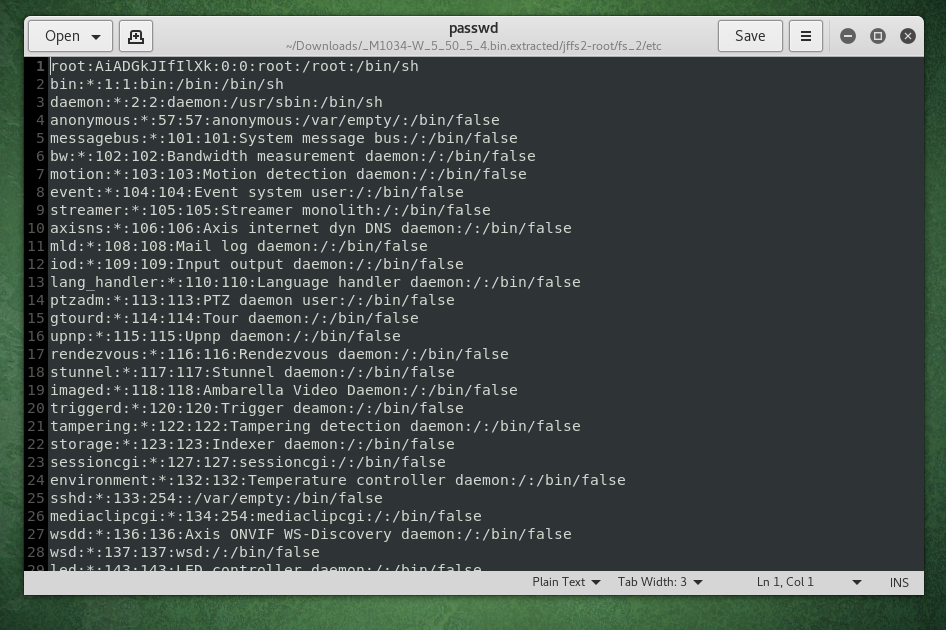
This isn’t a shadow file, this is a great indicator that we can decrypt the root password below:
root:AiADGkJIfIlXk:0:0:root:/root:/bin/sh
AiADGkJIfIlXk = pass
=)
Lets make enumeration a little faster:
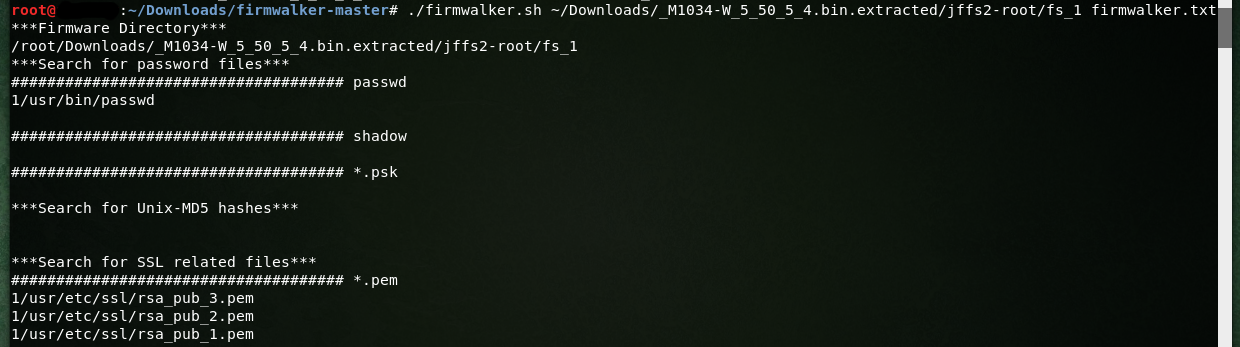
There is a great tool called firmwalker. It’s a simple bash script for searching the extracted or mounted firmware file system.
It will search through the extracted or mounted firmware file system for things of interest such as:
- etc/shadow and etc/passwd
- list out the etc/ssl directory
- search for SSL related files such as .pem, .crt, etc.
- search for configuration files
- look for script files
- search for other .bin files
- look for keywords such as admin, password, remote, etc.
- search for common web servers used on IoT devices
- search for common binaries such as ssh, tftp, dropbear, etc.
- search for URLs, email addresses and IP addresses
- Experimental support for making calls to the Shodan API using the Shodan CLI
After the application finished it’s extraction, the results will now help with narrowing down looking for the low hanging fruits: